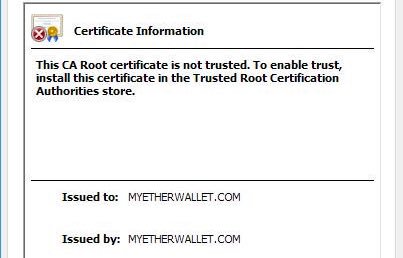
Amazon lost control of a small number of its cloud services IP addresses for two hours on Tuesday morning when hackers exploited a known Internet-protocol weakness that let them to redirect traffic to rogue destinations. By subverting Amazon's domain-resolution service, the attackers masqueraded as cryptocurrency website MyEtherWallet.com and stole about $150,000 in digital coins from unwitting end users. They may have targeted other Amazon customers as well.
The incident, which started around 6 AM California time, hijacked roughly 1,300 IP addresses, Oracle-owned Internet Intelligence said on Twitter. The malicious redirection was caused by fraudulent routes that were announced by Columbus, Ohio-based eNet, a large Internet service provider that is referred to as autonomous system 10297. Once in place, the eNet announcement caused Hurricane Electric and possibly Hurricane Electric customers and other eNet peers to send traffic over the same unauthorized routes. The 1,300 addresses belonged to Route 53, Amazon's domain name system service
In a statement, Amazon officials wrote: "Neither AWS nor Amazon Route 53 were hacked or compromised. An upstream Internet Service Provider (ISP) was compromised by a malicious actor who then used that provider to announce a subset of Route 53 IP addresses to other networks with whom this ISP was peered. These peered networks, unaware of this issue, accepted these announcements and incorrectly directed a small percentage of traffic for a single customer’s domain to the malicious copy of that domain."
eNet officials didn't immediately respond to a request to comment.
The highly suspicious event is the latest to involve Border Gateway Protocol, the technical specification that network operators use to exchange large chunks of Internet traffic. Despite its crucial function in directing wholesale amounts of data, BGP still largely relies on the Internet-equivalent of word of mouth from participants who are presumed to be trustworthy. Organizations such as Amazon whose traffic is hijacked currently have no effective technical means to prevent such attacks.
In 2013, malicious hackers repeatedly hijacked massive chucks of Internet traffic in what was likely a test run. On two occasions last year, traffic to and from major US companies was suspiciously and intentionally routed through Russian service providers. Traffic for Visa, MasterCard, and Symantec—among others—was rerouted in the first incident in April, while Google, Facebook, Apple, and Microsoft traffic was affected in a separate BGP event about eight months later.


 Loading comments...
Loading comments...
