Researchers have revealed a never-before-seen piece of cross-platform malware that has infected a wide range of Linux and Windows devices, including small office routers, FreeBSD boxes, and large enterprise servers.
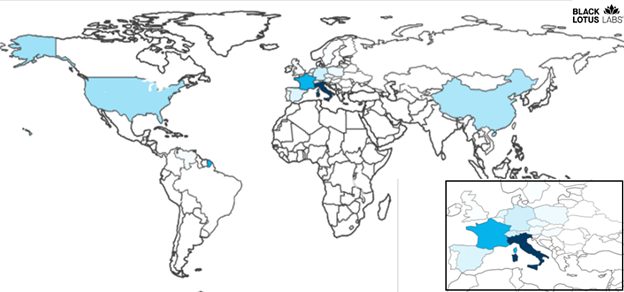
Black Lotus Labs, the research arm of security firm Lumen, is calling the malware Chaos, a word that repeatedly appears in function names, certificates, and file names it uses. Chaos emerged no later than April 16, when the first cluster of control servers went live in the wild. From June through mid-July, researchers found hundreds of unique IP addresses representing compromised Chaos devices. Staging servers used to infect new devices have mushroomed in recent months, growing from 39 in May to 93 in August. As of Tuesday, the number reached 111.
Black Lotus has observed interactions with these staging servers from both embedded Linux devices as well as enterprise servers, including one in Europe that was hosting an instance of GitLab. There are more than 100 unique samples in the wild.
"The potency of the Chaos malware stems from a few factors," Black Lotus Labs researchers wrote in a Wednesday morning blog post. "First, it is designed to work across several architectures, including: ARM, Intel (i386), MIPS and PowerPC—in addition to both Windows and Linux operating systems. Second, unlike largescale ransomware distribution botnets like Emotet that leverage spam to spread and grow, Chaos propagates through known CVEs and brute forced as well as stolen SSH keys."
CVEs refer to the mechanism used to track specific vulnerabilities. Wednesday's report referred to only a few, including CVE-2017-17215 and CVE-2022-30525 affecting firewalls sold by Huawei, and CVE-2022-1388, an extremely severe vulnerability in load balancers, firewalls, and network inspection gear sold by F5. SSH infections using password brute-forcing and stolen keys also allow Chaos to spread from machine to machine inside an infected network.
Chaos also has various capabilities, including enumerating all devices connected to an infected network, running remote shells that allow attackers to execute commands, and loading additional modules. Combined with the ability to run on such a wide range of devices, these capabilities have led Black Lotus Labs to suspect Chaos "is the work of a cybercriminal actor that is cultivating a network of infected devices to leverage for initial access, DDoS attacks and crypto mining," company researchers said.




 Loading comments...
Loading comments...
