Google researchers said on Wednesday they have linked a Barcelona, Spain-based IT company to the sale of advanced software frameworks that exploit vulnerabilities in Chrome, Firefox, and Windows Defender.
Variston IT bills itself as a provider of tailor-made information security solutions, including: technology for embedded SCADA (supervisory control and data acquisition) and Internet of Things integrators; custom security patches for proprietary systems; tools for data discovery; security training; and the development of secure protocols for embedded devices. According to a report from Google’s Threat Analysis Group, Variston sells another product not mentioned on its website: software frameworks that provide everything a customer needs to surreptitiously install malware on devices they want to spy on.
Researchers Clement Lecigne and Benoit Sevens said the exploit frameworks were used to exploit n-day vulnerabilities, which are those that have been patched recently enough that some targets haven't yet installed them. Evidence suggests, they added, that the frameworks were also used when the vulnerabilities were zero-days. The researchers are disclosing their findings in an attempt to disrupt the market for spyware, which they said is booming and poses a threat to various groups.
“TAG’s research underscores that the commercial surveillance industry is thriving and has expanded significantly in recent years, creating risk for Internet users around the globe,” they wrote. “Commercial spyware puts advanced surveillance capabilities in the hands of governments who use them to spy on journalists, human rights activists, political opposition, and dissidents.”
The researchers went on to catalog the frameworks, which they received from an anonymous source through Google’s Chrome bug reporting program. Each one came with instructions and an archive containing the source code. The frameworks came with the names Heliconia Noise, Heliconia Soft, and Files. The frameworks contained “mature source code capable of deploying exploits for Chrome, Windows Defender, and Firefox,” respectively.
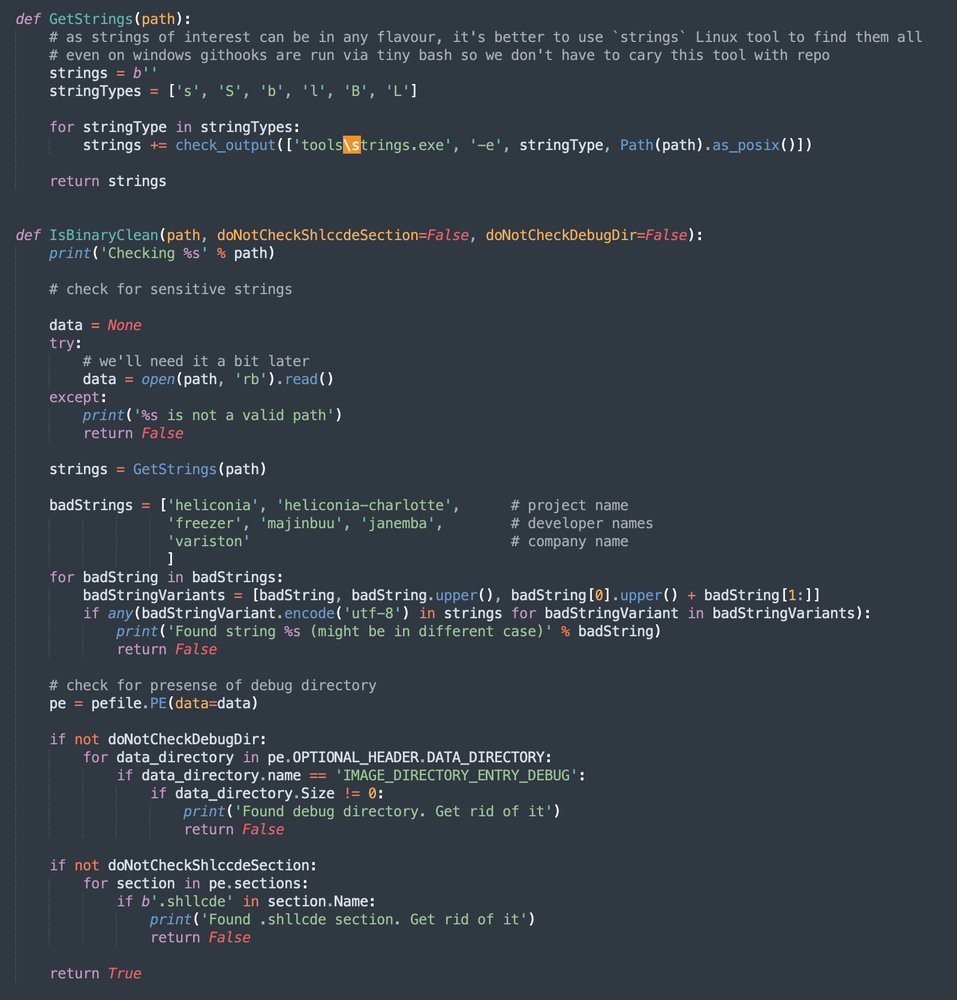
Included in the Heliconia Noise framework was code for cleaning up binary files before they are produced by the framework to ensure they don’t contain strings that could incriminate the developers. As the image of the cleaning script shows, the list of bad strings included “Variston.”


 Loading comments...
Loading comments...
